Blog posts
![[0x9] New DFIR-FI site](/images/blog/default_post.png)
[0x9] New DFIR-FI site
By whois
June 20, 2024 | One minute read
New year, new site
I have decided to merge my old sites blog.dfir.fi and dfir.fi into one page. I will also be posting about the DFIR-FI community, news about my new training courses, maintaining my CV, and promoting my services on this site.
Collaboration
At the same time as I launch the new site, I will also offer others the opportunity to post information on the site, both through the promotion of their company’s DFIR services and trainings and through blog posts. I look forward to hearing from anyone who would like to write about their DFIR research, malware, training experiences or any training-related blog posts on this site.
![[0x8] Log4shell memos](/images/blog/log4j.png)
[0x8] Log4shell memos
By whois
December 18, 2021 | 10 min read

Image source: Kevin Beaumont, Twitter
On Friday 10th of December 2021, internet was set on fire. Or technically internet was full of flammable material and someone shared matches to everyone on that day. In this blog post, I will present my thoughts about the case.
TL;DR
- Do not flame the developers of Log4j or open-source stuff in general for this issue
- Always use the newest version of Log4j
- If patching or mitigating is not possible in short term, organizations should consider taking down the vulnerable service until it has been fixed
- Use default deny outbound
- Assume breach
- Happy hunting!
What’s Log4shell and why everyone is buzzing about it ?
Log4shell is a vulnerability found from versions 2.X of Log4j. The vulnerability is easy to exploit and allows an attacker to run their own code in the target system (Remote Code Execution, RCE). The seriousness of the Log4shell vulnerability cannot be exaggerated.
![[0x7] Migration to Github](/images/blog/github.png)
[0x7] Migration to Github
By whois
September 23, 2021 | One minute read
I’ve decided to change my blog from self-hosted jekyll site to auto deployed Github hugo page.
Because of this, my blog’s RSS feed will also change. You can find the new RSS link from footer.
I will likely release more but less structured content on this blog in the future.
blog.dfir.fi CNAME will soon point to https://who1s.github.io
![[0x6] Cyber Security Essentials CTF](/images/blog/default_post.png)
[0x6] Cyber Security Essentials CTF
By whois
July 23, 2020 | 25 min read
Cyber Security Essentials is a course series I was organizing in HelSec with Future Female. CSE had 6 lectures and the CTF was organized at the end of the course. The course was aimed for female who are interested working in technical side of the Cyber Security OR just started in the field. This CTF was made 99% by me alone and was purposed to be entry level. More information about the course series can be found from here.
![[0x5] Phishing MFA accounts](/images/blog/default_post.png)
[0x5] Phishing MFA accounts
By whois
July 22, 2020 | 3 min read
MFA is usually considered secure. It however can be bypassed by phishing. I made this phishing demo using drk1wi’s tool Modlishka. The tool default templates are little bit outdated so here’s also instructions how to make it work against G-Suite accounts. This is not a new thing, I just wanted to check if it still works. =)
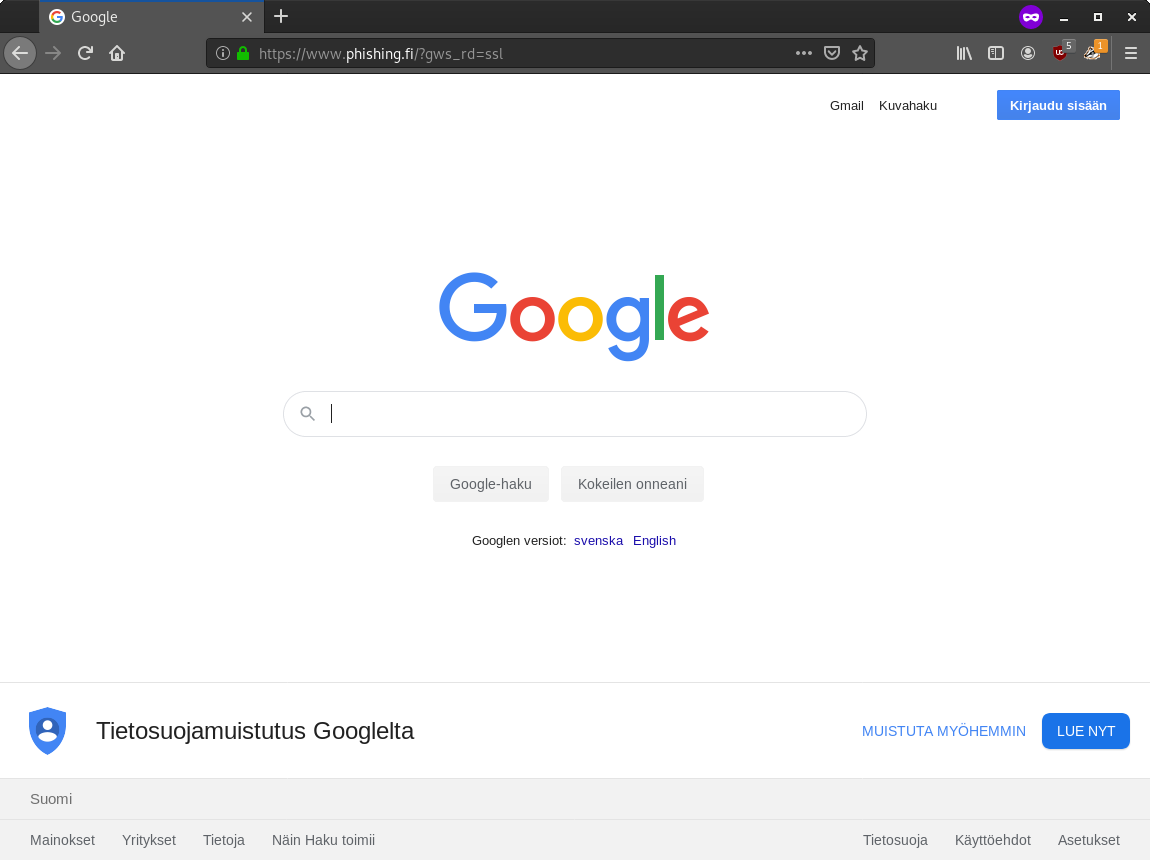
The full configuration is on Github.
Demo
Put it to the container
I decided to do quick and dirty dockerization for the tool:
![[0x4] Installing RegRipper on Linux](/images/blog/default_post.png)
[0x4] Installing RegRipper on Linux
By whois
February 19, 2020 | 3 min read
RegRipper is a tool made by H. Carvey (keydet89) for Windows registry analysis. The tool is perl script that is made to run on Windows. The tool can be installed on Linux distros but I haven’t yet found good instructions how to do it to share so I decided to make my own. I use the tool on the forensic courses I teach. Kudos to keydet89 for making this awesome tool.
![[0x3] Disobey 2020 puzzle writeup](/images/blog/default_post.png)
[0x3] Disobey 2020 puzzle writeup
By whois
December 23, 2019 | 20 min read

Disobey is a Finnish hacker/cyber security conference. They release every year a hacker challenge and 50 first who solve it, get to buy the special “hacker ticket” with a cheaper price than a regular ticket. The badge that comes with the ticket is also visually different looking than a normal ticket. At the first I have to admit, this year the challenge was harder than in previous years. This was my third time I tried to do the challenge and the third time I managed to solve it. As the challenge started at the same weekend as Assembly LAN party was held, we decided to give it a try together with Dist and Jaroneko as a team. There’s probably multiple different ways to solve it but here’s my take with some arguments why I did what I did. Hope you enjoy the read and even learn something from it!
![[0x2] Late wedding gift](/images/blog/default_post.png)
[0x2] Late wedding gift
By whois
July 7, 2019 | 6 min read

This is kinda old story but I wanted to share it with you as I find it somewhat funny. Sadly now, when I finally had spare time to spend with the document, the host it tries to connect is down. Hopefully you still enjoy the read!
Me and my wife got married 1,5 years ago in Las Vegas. As usual, I had to confirm the reservation by sending an email to the chapel. Everything went fine and the wedding session was good. Few months after the wedding trip, I got unexpected reply email from the chapel with somewhat suspicious attachment. The sender used the same signature than the legit clerk used before. Only the email address in the signature was different. Also, the address the email software rendered was different but it was still in the same legit domain.
![[0x1] SANS 2019 & BSides Orlando](/images/blog/bsides_orlando.jpeg)
[0x1] SANS 2019 & BSides Orlando
By whois
April 18, 2019 | 6 min read
Few weeks ago I left cold Finland and headed to Orlando to attend SANS FOR610 (Reverse-Engineering Malware). After signing up and buying flight tickets, I noticed that BSides Orlando was held just few days before the course started. I though “What the hell” and bought a ticket to that event as well. BSides is Disobey (Finnish hacking/cyber security event) like event and has talks, workshops, CTF, soldering station etc…
![[0x0] Hello World!](/images/blog/default_post.png)
[0x0] Hello World!
By whois
April 14, 2019 | One minute read
I decided to start blogging because
- I suck at remembering stuff -> If I write it publicly down, I will most likely remember it
- There’s no DFIR blogs in Finland (at least I don’t know of them)
- There’s never too many projects, right?
My bio can be found on about-page
