Tools blog posts
![[0x6] Cyber Security Essentials CTF](/images/blog/default_post.png)
[0x6] Cyber Security Essentials CTF
By whois
July 23, 2020 | 25 min read
Cyber Security Essentials is a course series I was organizing in HelSec with Future Female. CSE had 6 lectures and the CTF was organized at the end of the course. The course was aimed for female who are interested working in technical side of the Cyber Security OR just started in the field. This CTF was made 99% by me alone and was purposed to be entry level. More information about the course series can be found from here.
![[0x5] Phishing MFA accounts](/images/blog/default_post.png)
[0x5] Phishing MFA accounts
By whois
July 22, 2020 | 3 min read
MFA is usually considered secure. It however can be bypassed by phishing. I made this phishing demo using drk1wi’s tool Modlishka. The tool default templates are little bit outdated so here’s also instructions how to make it work against G-Suite accounts. This is not a new thing, I just wanted to check if it still works. =)
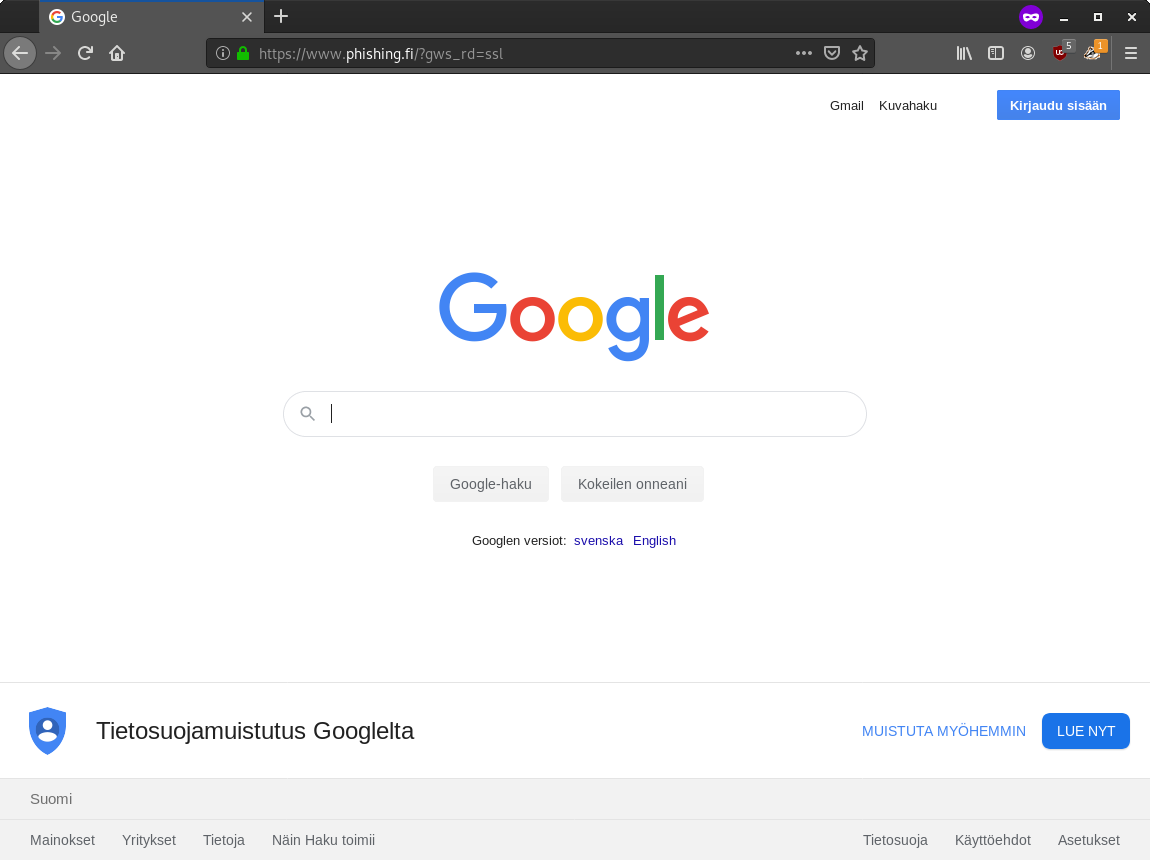
The full configuration is on Github.
Demo
Put it to the container
I decided to do quick and dirty dockerization for the tool:
![[0x4] Installing RegRipper on Linux](/images/blog/default_post.png)
[0x4] Installing RegRipper on Linux
By whois
February 19, 2020 | 3 min read
RegRipper is a tool made by H. Carvey (keydet89) for Windows registry analysis. The tool is perl script that is made to run on Windows. The tool can be installed on Linux distros but I haven’t yet found good instructions how to do it to share so I decided to make my own. I use the tool on the forensic courses I teach. Kudos to keydet89 for making this awesome tool.
![[0x3] Disobey 2020 puzzle writeup](/images/blog/default_post.png)
[0x3] Disobey 2020 puzzle writeup
By whois
December 23, 2019 | 20 min read

Disobey is a Finnish hacker/cyber security conference. They release every year a hacker challenge and 50 first who solve it, get to buy the special “hacker ticket” with a cheaper price than a regular ticket. The badge that comes with the ticket is also visually different looking than a normal ticket. At the first I have to admit, this year the challenge was harder than in previous years. This was my third time I tried to do the challenge and the third time I managed to solve it. As the challenge started at the same weekend as Assembly LAN party was held, we decided to give it a try together with Dist and Jaroneko as a team. There’s probably multiple different ways to solve it but here’s my take with some arguments why I did what I did. Hope you enjoy the read and even learn something from it!